Conference Paper:
Introduction
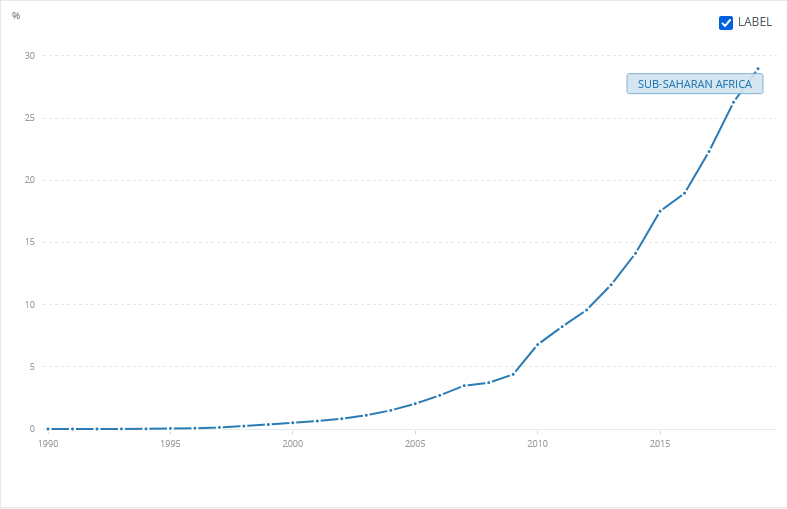
Internet penetration continues to be on the rise in Africa. Individuals using the internet in sub-Saharan Africa alone has risen from only 6.7% in 2010 to about 30% in 2019 (See Figure 1). Moreover, the use of the Internet is expanding beyond the cities and out to the low-income groups and uneducated in Africa. Vulnerable groups like the elderly and children are also being connected.
Financial inclusion usually targets the unbanked population of the continent, using technology and the Internet to bring about innovation and disruption in the financial services industry. More and more government services are being digitized, requiring everyday citizens to use the Internet to access these basic services. Yet, the majority of the community is not aware of the threats and dangers of using digital services.
The Problem
Cyber attacks are growing daily. A report from Interpol[1] reveals that despite the relatively low connectivity on the continent, cyber crime is on the rise from the continent. But it is not only the common citizen who is vulnerable to these threats, even large organizations and the tech savvy individuals in the society are not immune from online attacks. Organized cyber criminals have found the sharp rise in digital banking and mobile money accounts as lucrative targets for cyber crime. Internet users in Africa either lack the knowledge to properly set-up their accounts with basic cybersecurity best practices like using complex passwords, changing passwords frequently or using multi-factor authentication or are too lazy to do it, despite these features being available on most Internet services today.
Micro, small and medium-sized enterprises (MSMEs) make up 80% of all businesses in Africa[2]. With very little turnover and limited access to financing, these organizations often cannot afford nor have adequate incentives to invest in cybersecurity. This is not to say some of these businesses do not understand the risk of poor cybersecurity to their operations. Some do, but the majority don’t. In a recent research carried out in West and Central Africa, it was found that most businesses, both small and large were unsure if they had a cybersecurity skill gap or not[3] . This lack of resources and capability to defend themselves often make small businesses to be perceived as easy targets by cyber criminals. The impact to small businesses is likely to be more painful than a bigger business. If a small businesses loses their investment or intellectual property to a cyber attack, it might be impossible for them to recover.
Governments, policy makers and service providers must therefore think of innovative ways of protecting these lot who can clearly not defend themselves from cyber threats and happen to be make up the majority of our community.
The Solution…but first, the Debate
For decades, there’s been a debate on what role or how much ISPs should be involved in the security of the Internet. Arguments for a more involved role have centered around the fact that ISP have a vantage position on the pipe. Supporters of a more involved ISP in cybersecurity on the Internet, usually companies under Distributed Denial of Service (DDoS) attacks often ask ISPs to perform deep packet scans, to monitor traffic and shutdown suspicious activities.
On the other hand, those arguing against a more involved role by ISPs, the ISPs sit on this side of the debate, cite privacy concerns, possibility of false positives, liability concerns when promises of a safe network are made to customers and the fact that it takes all stakeholders to secure the Internet.
It is now widely acknowledged that no single stakeholder can address cybersecurity alone. Coordination between government, law enforcement, industry and the community is necessary in addressing cyber threats. The proposal this paper makes is not for any scanning of consumer traffic that is not already done today. Nor is it a proposal for ISPs to commit to a completely safe Internet connection delivered to the consumer or a claim that ISPs can single-handedly solve cybersecurity issues on the Internet. Rather, the proposal is for ISPs to scan for well-known threats, bad stuff, and malware command and control communication, then warn customers or block the malware. It is not a proposal to replace end-user security, but rather compliment it. Finally, the proposal’s primary focus is not enterprise networks, but rather on Internet connectivity to individual users and small businesses.
Network Security by Default
One of the most effective and innovative security intervention to the cybersecurity problem involves providing ‘invisible’ security to users. Such a concept exists today at the operating system level, in the form of automatic security updates which requires no intervention nor skill on the part of the customer and anti-malware features. Internet browser like Firefox, Chrome and Microsoft Edge have something similar. Google Safe Browsing on Chrome automatically identifies potentially harmful websites and warn users or prevent them from visiting such sites. Microsoft Defender SmartScreen does the same. It protects Internet users from phishing or malware websites and applications, and the downloading of potentially malicious files. It does this by looking for indications of suspicious behavior and checking the visited sites against a dynamic list of reported phishing sites and malicious software sites
Internet Service Providers could provide a similar service to users at the network layer by default too. Conceptually, the solution should include (1) the capability to identify threats like internet locations hosting malware, malware command and control communication, malicious code and malformed packets used in attacks and (2) have some ability to proactively act on those threats. Action could be just a warning to the customer or blocking attack traffic. These capabilities should be invisible to the customer, not requiring them to have any cyber defense skills. The ISP networks would be design by default with such capability. Most ISPs are likely to already have similar systems in place to protect their own corporate networks and sometimes to some extent, their customers.
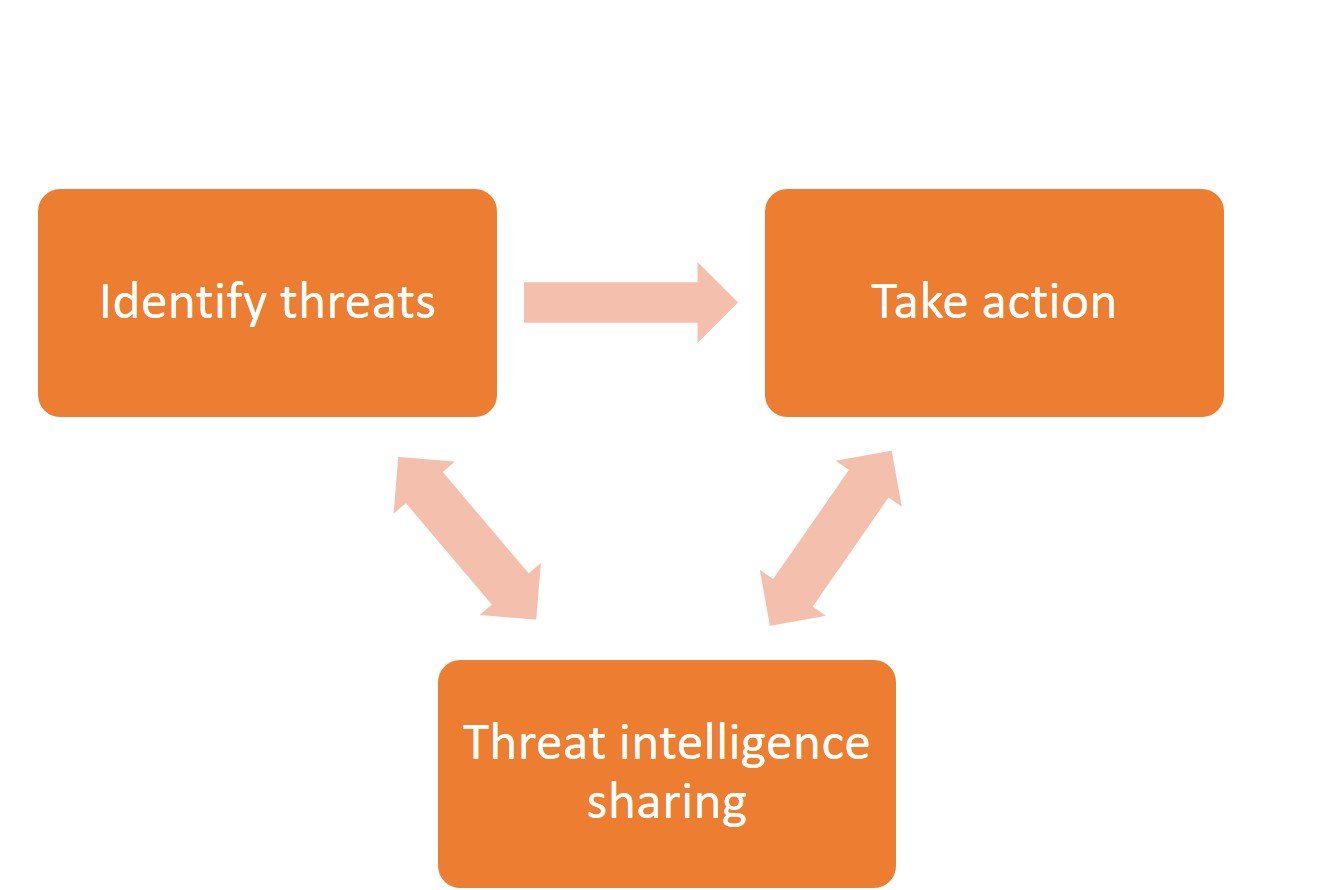
Another aspect of the proposal is collaboration and information sharing between ISPs. The benefit of this could be twofold. Firstly, it could improve the quality of the list of known malware or dangerous network traffic and further protect customers. Secondly, ISPs could take action on receipt of information about potentially harmful traffic.
It is not possible to completely eliminate the risk of cyber attacks and that is not what such an initiative should try to do. However, this could possibly see millions of attempted malware communications blocked and thereby significantly reducing the volume and impact of cyber attacks on defenseless consumers.
There are many advantages for protecting customers by default at the pipe level. Besides network operators being in a unique position to see the complete IP traffic and indicators where browser and OS providers cannot see or act, it allows for scalable protection to an entire customer base.
While such an implementation is rare today, it is not new. British Telecom runs an initiative called ‘proactive protection’[4], where malware communication is automatically blocked for hundreds of millions of customers monthly. Telstra also has a similar initiative which they call ‘cleaner pipes’[5]. Like with BT’s initiative, millions of malware communications are being proactively and automatically blocked every week as they try to cross Telstra’s infrastructure, thereby reducing the cyber threat on millions of their customers.
Unlike other regions and countries where a large proportion of users and businesses are cybersecurity aware and have resources to invest in defending themselves online, African users and organizations lack the resources and capacity. Protecting them at the network level by default could be a lifesaving solution to Africa.
[1] INTERPOL, ‘Online Crime in Africa a Bigger Threat than Ever before, INTERPOL Report Warns’ (Interpol, 2020), https://www.interpol.int/en/News-and-Events/News/2020/Online-crime-in-Africa-a-bigger-threat-than-ever-before-INTERPOL-report-warns.
[2] Moona Mupotola, ‘Small Businesses Key to Economic Growth in Africa’, International Trade Forum (blog), 9 December 2020, https://www.tradeforum.org/article/Small-businesses-key-to-economic-growth-in-Africa/.
[3] ‘Reports – GEFONA’, accessed 2 October 2021, https://gefona.org/rapports/.
[4] Dave Harcourt, ‘BT’s Proactive Protection: Supporting the NCSC to Make Our Customers Safer’, 25 October 2018, https://www.ncsc.gov.uk/blog-post/bts-proactive-protection-supporting-ncsc-make-our-customers-safer.
[5] Andrew Penn, ‘Safer Online and the New Normal’, Telstra Exchange, 5 May 2020, http://exchange.telstra.com.au/safer-online-and-the-new-normal/.


